Cybercrime has increased manyfold in the past few years, as it was ranked fifth in 2020 for the top risks and will be doubled in 2025. It caused global spending on cyber security to rise to reach $1 trillion in 2021, according to the report of Terranova. Not just this, the market size of cyber insurance is also predicted to have a value of USD 20 billion by 2025.
These emerging trends of cyber-attacks and in return meeting the new cyber security policies have generated the need to create an impactful cyber security dissertation.
Creating a strong and compelling dissertation on cybersecurity is like breaking down boundaries and becoming a cyberwarrior. However, this challenging task makes students fear it, and they need help figuring out how to write these papers well. If you are also going through a similar situation, don’t worry as you are not alone here!
To cope with this condition, students mostly prefer to ask for assistance from dissertation writing services. With highly experienced subject specialist writers, they provide instant solutions to all your queries and problems.
Here, we will crack the code by simply portraying ten easy tips to write your cyber security dissertation like a pro. We will also explore its basic structure and research topics and study the types of cybersecurity in detail. But before everything, you need to know what cyber security actually is.
What is Cyber Security?

Source: educba.com
According to the National Cyber Security Center, cyber security is all about keeping ourselves and our digital devices safe from cyber-attacks. Whether it’s our smartphones, laptops, or tablets, cyber security helps protect them from theft or damage. It’s also about safeguarding our personal information stored online and, on our devices, and making sure that only authorised people can access it.
In today’s world, cyber security is essential for our everyday activities. From banking and shopping online to using email and social media, we rely on it to keep our accounts, data, and devices secure. Without cyber security measures in place, we’d be vulnerable to cyber criminals who could exploit our digital lives.
Cyber Security Dissertation Ideas

Source: linkedin.com
As a beginner, you may face challenges starting to work on your dissertation without having any motivation and inspiration. You just need a spark of idea, but you just get stuck in with a blank mind. We understand this situation well when you want to work, but you are not able to brainstorm new ideas.
So, to help you in this situation, we have come up with a list of some cyber security dissertation ideas that you can easily use. Choose the one that best suits you and start your project as soon as possible.
- Protection Against Cyber Threats
- Unveiling the Invisible Techniques in Cyber Security
- Navigating the Cybersecurity Landscape
- Exploring the History and Theories of Cybersecurity
- Practical Applications of Cybersecurity
Top 10 Cyber Security Dissertation Topics for 2024
Well, after getting an idea about your cybersecurity field and the subject, you will start exploring the best topic for you. We understand the heart-wrenching hard work and struggle behind it, so we compiled a list of top trending dissertation topics for 2024. It not only eases your burden but also gives you inspiration to start right away.
The following are some unique and the best cyber security dissertation examples that you can use to get an idea for your own:
- Critical Infrastructure Security for Safeguarding Mission-Critical Assets
- Exploring Cyber Threats and Understanding Security Measures
- Cloud Security Strategies Against Cyber Attacks and Defend Against Threats
- Protecting Sensitive Information by Securing Devices in the Network Layer
- Machine Learning in Cybersecurity to Enhance Defenses
- Application Security to Safeguard Mobile Devices
- Cutting-Edge Trends in Computational Intelligence
- Securing Cloud Services to Prevent Cache Attacks
- Cybersecurity Strategies to Minimise Data Breaches
- Innovations in Cryptography for Hardware and Software
10 Top Tips for Cyber Security Dissertation Writing Excellently

Source: forbes.com
So, after getting an idea of topics, you are now ready to delve into the exciting as well as demanding phase of dissertation writing. No one can beat you unless you follow the right guidelines at the right time.
We have also been through similar situations, so we understand the value of perfect assistance at this stage. Students often consult dissertation helpers to avail of help with cyber security dissertations online. They provide the best suggestions and aid students to make their projects excellent.
The following are some simple and straightforward tips that you must follow before starting to write this significant task.
1. Start with a Strong Research Question
A research question matters in a dissertation for cyber security, as it is the key to opening the doors of your whole project. It directs your readers and talks about the in-depth study in a short and easy way. You must make your cyber security dissertation questions clear, concise and precise while giving equal importance to relevancy.
Furthermore, it should not confuse your readers so try to make it very clear and answerable for you. You should select your questions that are neither too broad nor too short to explain the essence of your topic. It should be researchable and also provoke analytical thinking and reasoning.
2. Write a Strong Introduction
The introduction is the starting point of your cyber security dissertation structure to describe your topic and research. It gives readers a thorough understanding of the goals, importance, and scope of your study. A concise thesis statement, a justification for the study, and background information on the subject are all necessary components of a strong introduction.
Furthermore, you should set the stage for your research here explaining cyber security in a larger context. You should keep your language and style formal but make it both interesting and educational as well.
3. Structure Your Literature Review Strategically
The second chapter is a thorough literature study and a writing of the research evaluations. Here, you have to go strategically through the sea of already existing literature and find the relevant content. You should choose the right way of doing this, like finding and studying the content year-wise from the previous year to the coming one. During this step, you should also explore the research gaps that your cyber security dissertation can fill.
When it comes to finding the right literature from credible sources, always consult academic sites, books, Google Scholar, published research articles and journals. During research, you should take your copy and pen or a laptop to organise your research with references side by side. Then, write this important chapter to cover everything that your reader wants to know about your topic.
4. Choose the Right Methodology
You will find different types of research methodologies, but you have to choose the right one for you. Just like cyber tools, these methodologies also have their advantages and drawbacks. Commonly, we find three types of methodologies:
- Qualitative
- Quantitative
- Mixed
Quantitative research makes use of statistics and facts, while qualitative research investigates feelings and viewpoints. And the third type is when you mix both of these approaches together in your cyber security dissertations.
Now, it’s up to you what you choose for your work, depending on your work’s nature and the goals of the study. By carefully weighing the advantages and disadvantages of each strategy, you may choose the technique that will best help you achieve your research goals.
5. Present Your Findings Effectively
In the end, the right presentation of your results matters a lot so effective communication in it is very important. Keep your research from getting lost in words! To make your findings easier to read, use well-defined tables, graphs, and charts. It also helps you to make your results more impactful and accessible. Recall that images are your strongest defence against the dullness of your dissertation.
For both qualitative and quantitative results presentations, coherence and clarity are crucial in your cyber security dissertation. Furthermore, you should be sure to include a comprehensive description of your data analysis methods, showcasing your method’s rigour and transparency.
6. Discuss Your Results Thoroughly
So, now, it’s time to interpret your findings once you obtain them. Here, you have to discuss everything in detail and relate your results with the body of literature. Give an explanation of your results in the most appropriate way a non-technical person can also understand it. You should also make a connection between these results and your research topic and demonstrate how they bolster your claims.
In addition, discuss your research work or arguments that support the theories and also discuss any counterarguments if there are any. It gives you an open ground to think critically and share your views that really shine in your cyber security dissertation writing!
7. Discuss Research Limitations and Opportunities
As we all know nothing in research is flawless. Every research work comes with its limits as well that you must discuss in your dissertation. This field of cyber security may face issues with sample size, data gathering, or methodology.
So, you should also discuss the study’s shortcomings while demonstrating your potential directions for further investigation. This demonstrates your awareness of the wider picture and your willingness to learn more. It also helps you to acknowledge the limits and make recommendations for further study.
8. Write a Brief but Powerful Conclusion
Writing a short conclusion of your whole research project is the end of your cyber security dissertation. In this part, you should restate your thesis statement as well as highlight the larger implications of your study.
It is like a summary of your whole project that explains everything that has happened and what you can expect further. It also shows the impact of your work on cyber security in the future. You should cover the wider ramifications of your findings as well.
9. Focus on Referencing and Formatting
You should not allow mistakes to take control of your work and ruin it. Rather, spend enough time on editing and proofreading as well after completing your cyber security dissertation writing task. You should also check out the particular requirements set out by your institution for formatting, citation style, and margins.
However, if you find it tough and challenging, you can also get help from citation generators, as they provide a thorough guide about style guidelines. They allow you to add references in any of the styles recommended by your institute, such as APA or MLA, to make sure your references are accurate.
10. Seek Input and Make Thorough Revisions
Considering yourself an all-rounder and not asking for help is not the right approach for writing a cyber security dissertation, though. Regardless of the fact that you know everything well and have done a wonderful task, you should also consult your teachers, fellows and even subject matter experts. They give you different viewpoints to assist you in identifying unseen mistakes. It helps you to polish your work further by specifying and removing all the mistakes.
What Exactly Does Cyber Security Do?

Source: mindfireit.com
Cyber security’s main job is to keep our devices, like smartphones, laptops, and tablets, safe from harm, whether we’re online or at work. It’s all about using technology, processes, and controls to shield our systems, networks, programs, and data from cyber-attacks. The goal? To lower the chances of these attacks happening and to stop unauthorized people from messing with our systems, networks, and tech.
What Are the 5 Types of Cyber Security?
Well, there are many types of cyber security, and you can choose any one of them for your cyber security dissertation, but the common five types are the following:
Network Security
This kind of security guards against unwanted access, usage, interruption, and changes of the information and hardware on a computer network. The physical layer, data connection layer, network layer, transport layer, and application layer are some of the network levels at which network security policies may be applied.
Application Security
Software programs get a shield against unauthorized use, access, disclosure, interruption, alteration, and destruction by this kind of security. At many phases of the software development lifecycle, such as design, coding, testing, and deployment, application security measures may be put into place.
Information Security
Information availability, confidentiality, and integrity are all safeguarded by this kind of security. Organisational layers at which information security measures may be applied include the technological, administrative, and physical levels.
Cloud Security
Data security and workloads housed in cloud environments become critical as cloud computing usage soars. Ensuring data encryption, access control, and strong identity management procedures are very important in cloud security.
Security of the Internet of Things (IoT)
The ever-growing network of connected devices makes it essential to secure these endpoints. IoT security covers shielding actuators, sensors, and smart devices against flaws. Secure communication methods, firmware upgrades, and device authentication come under specific controls.
So, to write a cyber security dissertation, you can select any one of the types of security mentioned above, according to your interest and subject demands. Keep in mind that, it is not only the type that you choose but also the way of doing that task that really matters.
What is 7-Layer Security?
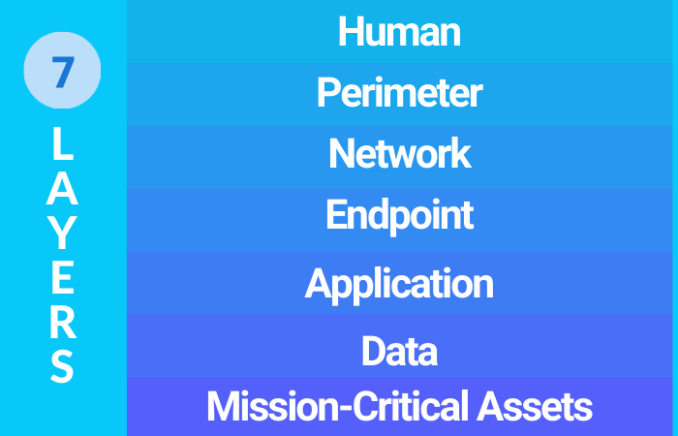
Source: manhattantechsupport.com
Back in the late 1970s, the International Standards Organization (ISO) realized that there needed to be a way to standardize how computers connected to each other. So, they came up with the Open Systems Interconnection (OSI) model. This model breaks down cybersecurity into seven layers, kind of like different levels of security on a network.
Here’s a quick rundown of the seven layers:
- Application Layer
- Human Layer
- Endpoint Layer
- Perimeter Layer
- Network Layer
- Data Layer
- Mission Critical Layer
Each layer represents a different part of how information moves through a network, from when a person types on a keyboard to how data is used by applications.
Conclusion
No doubt, writing a cyber security dissertation is not a piece of cake for everyone. It requires your exceptional efforts in research, writing and portraying the results well. You need to be careful throughout the process from planning to execution.
That’s why students often get tired of this demanding task and look outside for help. But to assist you with the best guide, we have provided some top-notch tips to streamline your tough journey. Furthermore, even after reading the above guidelines, if you think it is difficult to manage this task, seek guidance from cyber security dissertation writers to give an expert touch-up in your writing.





